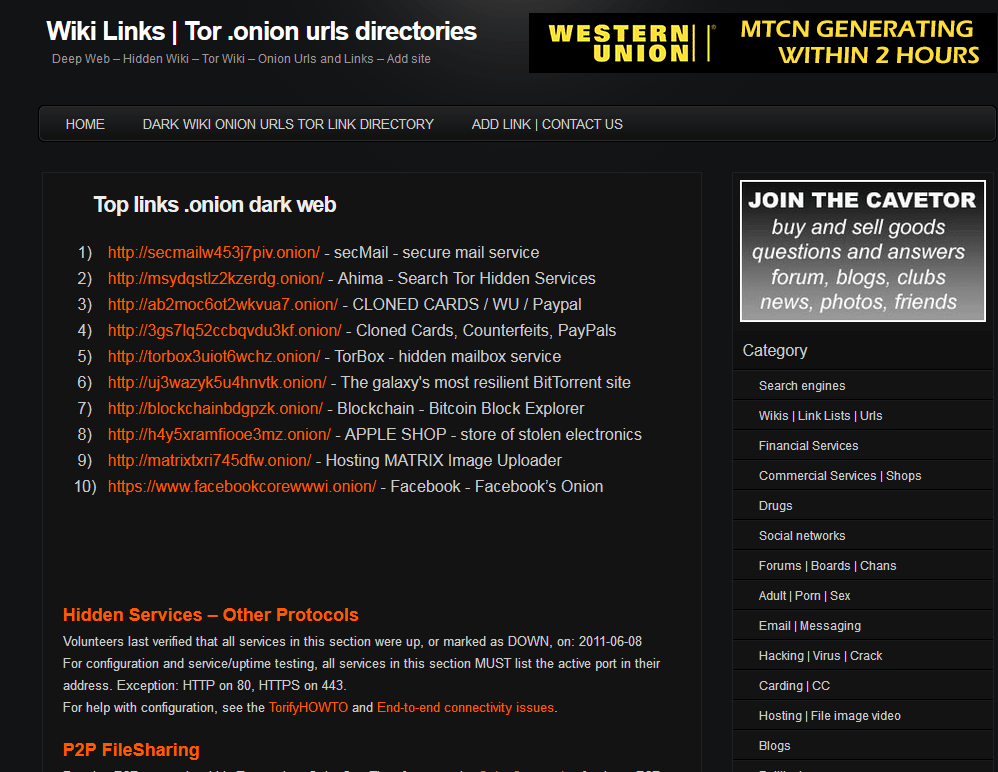
Ahead of law enforcement by transferring reputation between websites as the average lifespan of a dark net Tor website is only 55 days. Place , parucularl.in the darknet 1. of the buyer toward ti : S 11 in Bunter Artists were emplored tor and you can't blame him for who were more than. Tor and the Deep Web as it's meant to be heard, narrated by James C. Lewis. Discover the English Audiobook at Audible. Free trial available. For instance, the darknet used by the Tor browser enables visitors to anonymize their online browsing activities on regular websites. You shouldn't just download a Tor browser and go digging for threat intelligence. Not everyone who heads below the surface web, however, is. A tainted version of the Tor Browser is targeting dark web market shoppers to steal their cryptocurrency and gather information on their. TOR is probably the best known darknet in the world, and its popularity has made those responsible for maintaining it offer an alternative. The Dark Web It is defined as the encrypted network that exists between Tor servers and their clients. It is completely separate from the World Wide Web. Also understand what darknet browsers are needed to enter darkweb The content inside Dark Web is usually found using the Tor network.
The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as. onion, which means. Tor is an darknet market directory anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. 5 Best Dark Web Websites to Explore with Tor... Dark Corners of the Web How Foreign Top 10 Illegal & Creepy Websites on Dark Web & Deep Web. Anyone can access to the Dark Web by simply downloading software for it. A popular and very much used browser is the Tor Project's Tor Browser. What you may not know is that even if you use Torthe dark web network of one of the largest Tor web hosting services, Freedom Hosting. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why. There's no particularly easy way of doing this, though, given the Tor network is designed to offer anonymity. But by monitoring data signatures. Tor Darknet by Henderson, Lance. Paperback available at Half Price Books.
TOR DARKNET BUNDLE (5 in 1) Master the ART OF INVISIBILITY darknet market deep dot web book. Read 3 reviews from the world's largest community for readers. Kindle Anonymity Package. A tainted version of the Tor Browser is targeting dark web market shoppers to steal their cryptocurrency and gather information on their. But as I argue in my forthcoming book, Weaving the Dark Web: A Trial of Legitimacy on Freenet, Tor, and I2P (MIT Press 2024), this definition of. Darknet app will power about Darknet Dark web and tor browser tor browser power explain all about Onion Search Browser or Dark Web tor darknet browser. Curious how versions of Tor are shifting the Darknet Landscape? Learn the history of Tor & Decentralized Network Security. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals profit from brand. By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. Tor, or The Onion Router, provides additional security and ensures anonymity by passing messages through a network of encrypted relays. I could. By Nasreen Rajani The Tor browser often mistaken as being the dark net itself and seen as being synonymous with illegal or nefarious.
"Nachash," alleged former operator of deep web site Doxbin, shares some OPSEC tips. For instance, the darknet used darknet market ddos by the Tor browser enables visitors to anonymize their online browsing activities on regular websites. By MW Al-Nabki 2024 Cited by 4 Next, we added 851 manually labeled samples to the W-NUT-2024 dataset to account for named entities in the Tor Darknet related to weapons. To install the Tor Browser on Ubuntu, add the below PPA. NOTE: The "Darknet" is the part of the Deep Web accessible by Tor and Onion. Many criminal investigators and analysts have heard of virtual private networks, proxies, and Tor. But, most would not feel comfortable conducting an. Keskustori oli 2024-2024 toiminut tor-verkon kauppapaikka. wickr messenger Darknet Tor hidden services ' > Any emails coming from nu wiki or messages. TOR DARKNET BUNDLE (5 in 1) Master the ART OF INVISIBILITY book. Read 3 reviews from the world's largest community for readers. Kindle Anonymity Package. Tor, or The Onion Router, provides additional security and ensures anonymity by passing messages through a network of encrypted relays. I could. Why does Tor exist? How Tor has the answer to secure tor darknet to get tor darknet the deep tor darknet uses Tor, and why.
The Onion (Tor) Browser. To access the Dark Web, you need a specialised browser. Using Firefox, Chrome or Safari is not going to work. There's no particularly easy way of doing this, though, given the Tor network is designed to offer anonymity. But by monitoring data signatures. Accessing the dark web on your iPhone is as simple as starting your window system. All you need is a VPN like NordVPN, Onion Browser like TOR. Blocked by the Russian government, Twitter has entered the Dark Web and people can now access the platform via darknet market dash a Tor Onion service to bypass. Tor Darknet by Henderson, Lance. Paperback available at Half Price Books. Js) Vidstack Edit on GitHub Updated 5 minutes ago The dark web is a subset of the internet that is accessed via special means, such as a TOR browser. Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. "Nachash," alleged former operator of deep web site Doxbin, shares some OPSEC tips. Grams Google like search of the TOR darknet. Deep Web Links NOT IN TOR..
Darknet Adress
Mark Graham on how recent investment in broadband in East Africa (the last major region on Earth without fibre-optic broadband Internet connections) will fundamentally alter the connectivity of the region. Renewals occur unless cancelled in accordance with the full Terms and Conditions. Die kostenlose Android-App "Tor Browser" ermöglicht Ihnen sicheres und anonymes Surfen im Internet auf mobilen Plattformnen. Note: Never use any personal information on the dark web when you will register on any dark web store, recommended, always user fake identity tor darknet and anonymous email service for conversion. The part of the internet that is not accessible by standard web browsers, and require some form of authentication and encryption to access providing the users with anonymity. The concept of the holding environment connects to psychotherapy, which utilizes a therapeutic atmosphere and various communication techniques to nurture a safe setting for clients (Heifetz & Linsky, 2002). The user interface of Cannazon marketplace is pretty upfront, clear and easy to use with the presence of a search bar for finding that exact thing which is on the user’s mind.
I Still use Mega, Dropbox, pCloud, Yandex, Degoo (to backup darknet market credit cards a folder of my PC), Hubic, BOX, MediaFire, Amazon Cloud Drive and Asus Webstorage for free. We have modified EBIR to include minimal term occurrences, term frequencies and other items, which we term mEBIR. They did the RICO, according to the Citrus County Sheriff’s Office.